FortiGate AD-VPN Configuration with OSPF
Problem
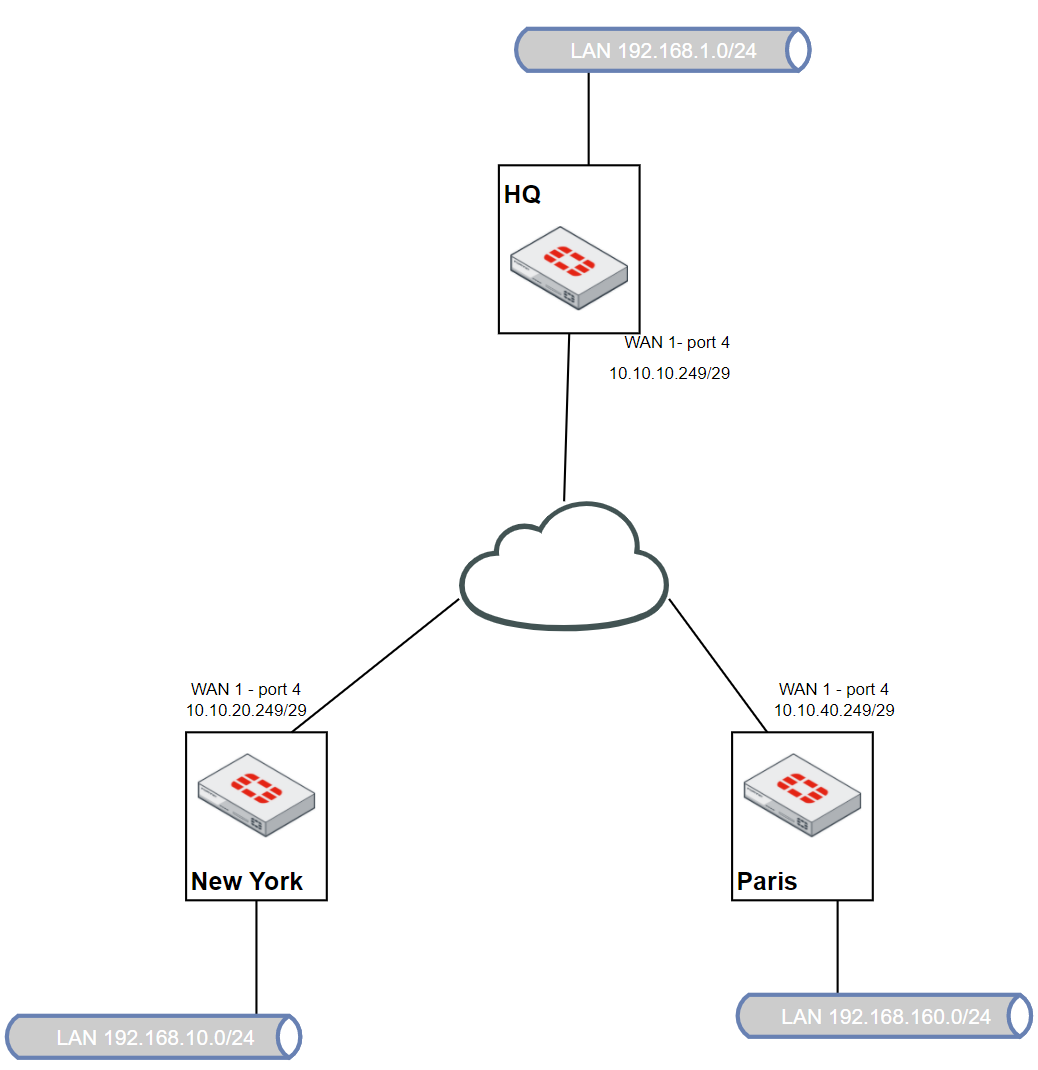
Several Branch Offices are connected to the HQ. In addition, the branches must also communicate each other. The configuration should be kept as simple and easy to maintain as possible.
Solution
There are several solutions on the internet to configure an AD-VPN (Branch to Hub IPsec with Shortcuts). In this tutorial I tried to keep the necessary steps as simple as possible.
In principle, a classic Hub2Spoke (star) topology is created. The only difference is that the routing is solved via OSPF and the VPN tunnel is allowed to create a shortcut VPN tunnel if necessary.
HQ
First, let's look at the necessary configuration in HQ:
IPsec
config vpn ipsec phase1-interface
edit "ADVPN-Hub"
set type dynamic
set interface "port4"
set ike-version 2
set peertype any
set net-device enable
set proposal aes256-sha256
set add-route disable
set dpd on-idle
set auto-discovery-sender enable
set psksecret fortinet
set dpd-retryinterval 60
next
end- net-device: create kernel device for this IPsec connection
- add-route: disable control addition of a route to peer destination selector
- auto-discovery-sender: enable the mechanism to send shortcut information to peers
config vpn ipsec phase2-interface
edit "ADVPN-Hub.P2"
set phase1name "ADVPN-Hub"
set proposal aes256-sha256
next
endInterfaces
Each interface need an IP address for OSPF comunication between the peers.
config system interface
edit "ADVPN-Hub"
set ip 172.17.30.254 255.255.255.255
set allowaccess ping
set type tunnel
set remote-ip 17.17.30.253 255.255.255.0
set snmp-index 16
set interface "port4"
next
end- ip: assign IP address to this tunnel interface. (You can joice IP Range as you want)
- remote-ip: this peer is the Hub and need no "remote-ip" but this field is mandatory. Enter a free IP address from your AD-VPN IP Range.
OSPF
Without shortcut VPN, the traffic is sent via the hub. The hub registers that a shortcut VPN is possible and sends the necessary information to the branch peer. After the shortcut VPN tunnel is open, the routing table must be changed dynamically. Only in this way is it possible for the traffic to flow through the shortcut VPN afterwards.
For this reason, it is mandatory to use a dynamic routing protocol for AD-VPN. Currently RIP, BGP and OSPF are possible.
The OSPF configuration is easy:
config router ospf
set router-id 192.168.2.1
config area
edit 0.0.0.0
next
end
config ospf-interface
edit advpn
set interface ADVPN-Hub
set retransmit-interval 1
set hello-interval 1
next
config network
edit 1
set prefix 172.17.30.0 255.255.255.0
next
edit 2
set prefix 192.168.2.0 255.255.255.252
next
end
end- retransmit-interval: Specify how long the routing device waits to receive a link-state acknowledgment packet before retransmitting link-state advertisements (LSAs) to an interface’s neighbors.
- hello-interval: this defines how often we send the hello packet.
As shorter the interval times are, as shorter the switching time to the shortcut tunnel is.
Branches
The Branches configuration is more or less the same as the Hub is.
IPsec
config vpn ipsec phase1-interface
edit "ADVPN-Branch"
set type dynamic
set interface "port4"
set ike-version 2
set peertype any
set net-device enable
set proposal aes256-sha256
set add-route disable
set dpd on-idle
set auto-discovery-receiver enable
set psksecret fortinet
set dpd-retryinterval 60
next
end- net-device: create kernel device for this IPsec connection
- add-route: disable control addition of a route to peer destination selector
- auto-discovery-receiver: enable the mechanism to recevice shortcut information from the hub.
config vpn ipsec phase2-interface
edit "ADVPN-Branch.P2"
set phase1name "ADVPN-Branch"
set proposal aes256-sha256
next
endInterfaces
Each interface need an IP address for OSPF comunication between the peers.
config system interface
edit "ADVPN-Branch"
set ip 172.17.30.2 255.255.255.255
set allowaccess ping
set type tunnel
set remote-ip 17.17.30.254 255.255.255.0
set snmp-index 16
set interface "port4"
next
end- ip: assign IP address from your Shurtcut Range to this tunnel interface.
- remote-ip: Enter the IP address from the Hub.
OSPF
The OSPF configuration is easy for Branches as well:
config router ospf
set router-id 2.2.2.2
config area
edit 0.0.0.0
next
end
config ospf-interface
set interface ADVPN-Branch
set retransmit-interval 1
set hello-interval 1
next
config network
edit 1
set prefix 172.17.30.0 255.255.255.0
next
edit 2
set prefix 192.168.160.0 255.255.255.252
next
end
endAdapt the configuration for the second Branch from this example.



Comments
Post a Comment